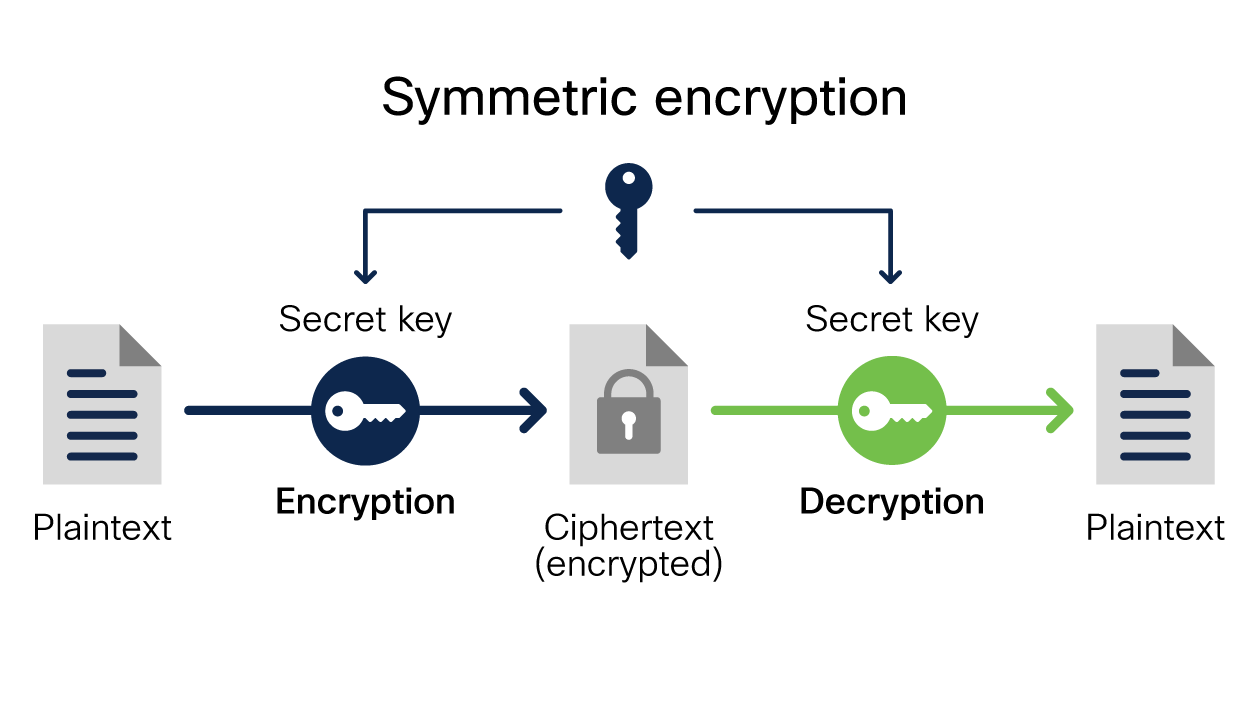
Hardware Encryption Secure . hardware encryption uses an onboarding device algorithm for encryption and decryption. these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices no longer put sensitive data at risk. Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. Learn why hardware encryption beats software encryption for law firm data. learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management.
from www.cisco.com
Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management. these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices no longer put sensitive data at risk. hardware encryption uses an onboarding device algorithm for encryption and decryption. Learn why hardware encryption beats software encryption for law firm data.
What Is Encryption? Explanation and Types Cisco
Hardware Encryption Secure learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management. hardware encryption uses an onboarding device algorithm for encryption and decryption. Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices no longer put sensitive data at risk. learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management. Learn why hardware encryption beats software encryption for law firm data.
From techcommunity.microsoft.com
Using Hardware Security Modules with Always Encrypted Microsoft Tech Hardware Encryption Secure hardware encryption uses an onboarding device algorithm for encryption and decryption. learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management. Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. these devices protect data in a fundamentally different. Hardware Encryption Secure.
From dxofweczu.blob.core.windows.net
How Does Hardware Encryption Work at Emilia Cox blog Hardware Encryption Secure learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management. Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. Learn why hardware encryption beats software encryption for law firm data. hardware encryption uses an onboarding device algorithm for encryption. Hardware Encryption Secure.
From omninet.io
Hardware Encryption Modules for the SMB My Digital Shield Hardware Encryption Secure Learn why hardware encryption beats software encryption for law firm data. Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. hardware encryption uses an onboarding device algorithm for encryption and decryption. learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security. Hardware Encryption Secure.
From windowsreport.com
5 best hardwareencrypted flash drives Hardware Encryption Secure hardware encryption uses an onboarding device algorithm for encryption and decryption. Learn why hardware encryption beats software encryption for law firm data. these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices no longer put sensitive data at risk. learn how encrypted hard drives use the rapid. Hardware Encryption Secure.
From www.virtru.com
KMIP & Hardware Security Modules Which is Best for Encryption? Virtru Hardware Encryption Secure Learn why hardware encryption beats software encryption for law firm data. Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. hardware encryption uses an onboarding device algorithm for encryption and decryption. learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security. Hardware Encryption Secure.
From www.itprotoday.com
External Hardware Encrypted Disks Weighing the Pros and Cons ITPro Hardware Encryption Secure these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices no longer put sensitive data at risk. hardware encryption uses an onboarding device algorithm for encryption and decryption. learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and. Hardware Encryption Secure.
From geekflareae.pages.dev
Hardware Encryption What It Is And Why You Need It geekflare Hardware Encryption Secure Learn why hardware encryption beats software encryption for law firm data. Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices no longer put sensitive data at risk. hardware encryption. Hardware Encryption Secure.
From www.otherarticles.com
Hardware Encryption Vs Software Encryption A Comprehensive Guide Hardware Encryption Secure learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management. Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices. Hardware Encryption Secure.
From www.epikshare.com
Overview What hardware security modules do for data encryption epiKshare Hardware Encryption Secure learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management. hardware encryption uses an onboarding device algorithm for encryption and decryption. these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices no longer put sensitive data at. Hardware Encryption Secure.
From gitlabcommitvirtual2021.com
Hardware encryption LabVirtual 2.0 Hardware Encryption Secure learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management. Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices. Hardware Encryption Secure.
From quizdbobtentions.z21.web.core.windows.net
Location Of Encryption Devices Hardware Encryption Secure hardware encryption uses an onboarding device algorithm for encryption and decryption. Learn why hardware encryption beats software encryption for law firm data. these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices no longer put sensitive data at risk. learn how encrypted hard drives use the rapid. Hardware Encryption Secure.
From medium.com
Secure Cryptographic Operations with Hardware Security Modules by Hardware Encryption Secure Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. hardware encryption uses an onboarding device algorithm for encryption and decryption. learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management. Learn why hardware encryption beats software encryption for law. Hardware Encryption Secure.
From nextdoorsec.com
Hardware Encryption vs. Software Encryption Safeguarding Data in the Hardware Encryption Secure Learn why hardware encryption beats software encryption for law firm data. hardware encryption uses an onboarding device algorithm for encryption and decryption. Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. these devices protect data in a fundamentally different way that provides a level of security so advanced that. Hardware Encryption Secure.
From www.synopsys.com
tRoot Vx HSM Synopsys Hardware Encryption Secure Learn why hardware encryption beats software encryption for law firm data. these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices no longer put sensitive data at risk. hardware encryption uses an onboarding device algorithm for encryption and decryption. Hardware encryption enhances security by storing the encryption keys. Hardware Encryption Secure.
From www.techspot.com
Apricorn releases world's largest hardwareencrypted portable SSD Hardware Encryption Secure hardware encryption uses an onboarding device algorithm for encryption and decryption. these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices no longer put sensitive data at risk. Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. Learn why. Hardware Encryption Secure.
From www.walmart.com
imation Secure+ HardwareEncrypted USB 2.0 Flash Drive, 16 GB Hardware Encryption Secure these devices protect data in a fundamentally different way that provides a level of security so advanced that lost devices no longer put sensitive data at risk. Learn why hardware encryption beats software encryption for law firm data. learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management.. Hardware Encryption Secure.
From m2pfintech.com
Cryptographic Keys and Hardware Security Modules An IntroductionM2P Hardware Encryption Secure hardware encryption uses an onboarding device algorithm for encryption and decryption. learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management. Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. these devices protect data in a fundamentally different. Hardware Encryption Secure.
From m2pfintech.com
Cryptographic Keys and Hardware Security Modules An IntroductionM2P Hardware Encryption Secure Hardware encryption enhances security by storing the encryption keys within the hardware device, reducing susceptibility to attacks or. learn how encrypted hard drives use the rapid encryption that is provided by bitlocker to enhance data security and management. Learn why hardware encryption beats software encryption for law firm data. these devices protect data in a fundamentally different way. Hardware Encryption Secure.